Access Your SSH Device From Anywhere: A Simple Guide To Remote Control
Imagine having the ability to manage your computers, servers, or smart gadgets from literally any place on Earth. It's a powerful idea, isn't it? For many, the thought of controlling a distant machine seems like something out of a science fiction movie, yet it's a very real and incredibly useful capability today. This kind of remote access is especially helpful for those who work with Linux systems or a growing number of connected devices around the home or office.
This comprehensive guide will walk you through the process, ensuring you can connect securely from anywhere with the right setup, as a matter of fact. Accessing your SSH device remotely opens a world of possibilities, from managing servers to securely transferring files. You see, being able to reach your own tech, no matter where you are, truly makes life easier and more efficient for so many people.
We're talking about taking full control of your Linux server or device with our comprehensive guide to SSH remote access from anywhere in the world. Yes, you can access your device from anywhere using SSH, but it requires some additional setup to ensure the connection is secure and reliable. This guide will walk you through everything needed to make that happen, you know, step by step.
- Ullu Actress List
- Khatrimaza Gujarati Movie Download
- Wwxxcom Reviews 2025
- Bailey Sarian
- Ayushi Jaiswal Webseries
Table of Contents
- Understanding SSH and Why It Matters
- Preparing Your Device for Remote Access
- Securely Connecting from a Distance
- Real-World Uses for Remote SSH
- Advanced Tips for Smoother Connections
- Frequently Asked Questions About Remote SSH
- Your Next Steps for Remote Access
Understanding SSH and Why It Matters
What Exactly Is SSH?
SSH, or Secure Shell, is a kind of network protocol. It provides a secure way to access a computer, you know, over an unsecured network. Think of it as a private, encrypted tunnel between your computer and the device you want to control. This tunnel keeps your commands and any information you send or receive completely private from prying eyes, which is pretty important.
Secure Shell (SSH) is a protocol that provides encrypted communication between devices, making it an ideal solution for IoT remote access. This means that when you're sending commands to your server or pulling files from your IoT device, the data is scrambled and protected. It's like sending a secret message in a coded language that only the sender and receiver can understand, you might say.
Without SSH, accessing a remote device would be like shouting your passwords and commands across a crowded room, totally exposed for anyone to hear. So, it's very, very important for keeping your digital life safe and sound. It truly is the backbone of secure remote control for so many systems.
Why Remote Access Is So Important
As the Internet of Things continues to grow, the ability to securely access and manage these devices from anywhere becomes increasingly important. Just imagine having smart home gadgets, security cameras, or even industrial sensors spread across different locations. You can't always be physically present to check on them or make adjustments, can you?
Accessing your SSH (Secure Shell) device remotely is crucial for managing servers, routers, and other network devices from anywhere with an internet connection. This saves a lot of time and effort, especially for IT professionals or anyone with multiple systems to look after. It's about efficiency and having control, more or less, without being tied to a specific location.
One common method to remotely access a Ubuntu Linux from anywhere is using Secure Shell (SSH), a network protocol that provides a secure way to communicate with a remote device. For businesses, this means administrators can fix issues on servers located thousands of miles away without leaving their desk. For individuals, it means you can check on your home server while on vacation, which is pretty neat.
Preparing Your Device for Remote Access
Getting Your Linux or IoT Device Ready
Before you can SSH device from anywhere, your target device needs to be set up properly. This usually means it's running a Linux-based operating system, like Ubuntu, or is an IoT device designed for remote management. You'll want to make sure the device is powered on and connected to the internet, naturally.
For Linux servers, this often involves making sure the operating system is up-to-date and that you have a user account with the necessary permissions. For IoT devices, it might mean checking the device's specific documentation for any initial setup steps related to network connectivity or remote access features. It's a bit like getting all your tools ready before starting a big project, you know.
You'll also want to make sure your device has a stable internet connection. To access your SSH device from anywhere, a reliable connection is absolutely needed. This might seem obvious, but a shaky Wi-Fi signal or an unreliable wired connection can cause a lot of headaches when you're trying to connect remotely, so keep that in mind.
Setting Up SSH on Your Device
The very first step is making sure an SSH server is running on the device you want to access. On most Linux distributions, this means installing and starting the OpenSSH server. For example, on Ubuntu, you might use a command like `sudo apt install openssh-server`, which is pretty straightforward.
Once installed, the SSH server typically starts automatically. You can check its status to confirm it's running correctly, perhaps with a command like `sudo systemctl status ssh`. This ensures that your device is listening for incoming SSH connections, which is essentially how it knows to respond when you try to connect from afar, you see.
For IoT devices, the SSH server might be pre-installed or require a specific firmware update or configuration through a web interface. It's important to follow the manufacturer's instructions very carefully here. Improper configuration can expose sensitive data and create vulnerabilities, so, you know, always be careful.
Network Configuration for Anywhere Access
This is often the trickiest part of getting your SSH device from anywhere. Your device is likely behind a router in your home or office network. For outside connections to reach it, you usually need to set up something called "port forwarding" on your router. This tells your router to direct incoming SSH requests (which typically use port 22) to your specific device's local IP address, in a way.
You'll need to log into your router's administration panel, usually by typing its IP address into a web browser. From there, look for sections like "Port Forwarding," "NAT," or "Virtual Servers." You'll then create a rule that forwards external port 22 (or a different, less common port for added security) to the internal IP address of your device on port 22. This is a bit like telling the mail carrier exactly which apartment number to deliver a package to, even though the building has one main entrance, actually.
Another important consideration is your public IP address. Many home internet connections use dynamic IP addresses, meaning they change occasionally. If your public IP changes, your remote connection will break. Services like Dynamic DNS (DDNS) can help with this by linking a fixed hostname (like `myhomedevice.ddns.net`) to your changing IP address. This way, you always connect to the same easy-to-remember name, even if the underlying IP address shifts, which is really helpful.
Securely Connecting from a Distance
Using SSH Clients on Different Machines
Once your target device and network are ready, you need an SSH client on the machine you're connecting *from*. If you're using a Linux or macOS computer, the SSH client is usually built right in. You just open a terminal and type `ssh username@your_device_ip_or_hostname`, like your own personal command center.
For Windows users, you can use the built-in OpenSSH client that comes with newer versions of Windows 10 and 11, which is quite handy. Alternatively, popular third-party clients like PuTTY have been around for a long time and are very reliable. These clients provide a simple interface to enter your connection details and get started, you know, without much fuss.
To effectively use SSH IoT from anywhere on Android, you'll need a reliable SSH client app. There are many good options available on the Google Play Store that let you connect to your devices using your phone or tablet. This means you can manage your IoT devices from anywhere in the world, as long as you have an internet connection, which is pretty amazing.
Extra Security Measures You Should Take
While SSH provides a secure communication channel, remote SSH login allows users to interact with IoT devices from anywhere in the world. But, improper configuration can expose sensitive data and create vulnerabilities. So, key to Ubuntu SSH remote access is not compromising your organizational security, or your personal security for that matter.
One of the most important security steps is to use strong, unique passwords for your SSH users. Better yet, switch to SSH key-based authentication. This uses a pair of cryptographic keys (one public, one private) instead of passwords, which is much more secure. You keep the private key safe on your local machine, and the public key goes on the remote device, you see.
Another good practice is to change the default SSH port (22) to a different, less common port. This won't stop a determined attacker, but it will reduce the amount of automated scanning and brute-force attempts against your device. Also, consider setting up a firewall on your remote device to only allow SSH connections from specific IP addresses if possible, which adds another layer of protection, you know.
Handling Common Connection Issues
Sometimes, despite your best efforts, you might run into connection problems. A common issue is incorrect port forwarding settings on your router. Double-check that the external port is correctly mapped to the internal IP address and port of your device. It's a very common spot for little mistakes, you might find.
Firewall settings on either your local computer or the remote device can also block SSH connections. Make sure that SSH traffic is allowed through any firewalls in place. If you're connecting from a public Wi-Fi network, some networks might block SSH ports, which can be a bit frustrating. In such cases, a VPN might be needed to bypass these restrictions, you know.
Another thing to check is the SSH service itself on the remote device. Is it running? Are there any error messages in its logs? Sometimes a simple restart of the SSH service can fix minor glitches. Also, verify that you're using the correct username and password (or SSH key) for the remote device, because, you know, small typos happen to everyone.
Real-World Uses for Remote SSH
Managing Servers from Far Away
For system administrators, the ability to SSH device from anywhere is absolutely essential. They can manage servers located in data centers across the globe, perform updates, troubleshoot issues, and deploy new applications without ever leaving their office. This saves a tremendous amount of travel time and keeps systems running smoothly around the clock, which is pretty vital.
Whether it's a web server, a database server, or a development machine, SSH provides the command-line access needed to perform almost any task. You can install software, configure services, check logs, and even restart the entire system, all from a remote terminal. It's like having your hands directly on the keyboard of the distant machine, you might say.
This capability is also a lifesaver for personal projects. If you have a home server for media streaming, backups, or hosting a small website, you can maintain it from anywhere. So, if you're on vacation and something goes wrong, you can usually fix it with a few commands, which is very convenient.
IoT Device Control from Anywhere
As the Internet of Things grows, managing numerous smart devices becomes a real challenge. SSH offers a secure and reliable way to access IoT devices, enabling you to control them remotely. By setting up SSH, you can conveniently manage your IoT devices from anywhere in the world, as long as you have an internet connection, which is really quite useful.
This is especially true for devices like Raspberry Pis, smart sensors, or custom-built home automation hubs. You can push software updates, adjust settings, collect data, or even reboot a device if it becomes unresponsive. It gives you a level of control that simple mobile apps often don't provide, honestly.
Out of many ways to connect them, Secure Shell (SSH) provides a secure and reliable way to access IoT devices. This means you can ensure your IoT environment is secure, reliable, and accessible, no matter where you are. It's about maintaining full command over your connected world, in a very direct way.
File Transfers and Data Management
Beyond just running commands, SSH is also fantastic for securely transferring files between your local machine and a remote device. Tools like `scp` (Secure Copy) or `sftp` (SSH File Transfer Protocol) use SSH to encrypt file transfers. This means your sensitive data stays protected as it moves across the internet, which is a very good thing.
You can upload new files to your server, download backups, or transfer configuration files with ease. This is much safer than using traditional FTP, which sends data unencrypted and leaves it vulnerable. So, for anyone dealing with important data, SSH-based file transfers are the way to go, you know.
This capability is particularly useful for web developers who need to deploy website updates or for users who want to pull large log files from a remote server for analysis. It simplifies data management significantly, making it possible to keep your remote systems updated and your local systems stocked with the information you need, pretty much instantly.
Advanced Tips for Smoother Connections
SSH Keys for Easier Logins
As mentioned before, SSH keys offer a more secure and convenient way to log in than passwords. Once set up, you won't need to type your password every time you connect, which saves a lot of time. You generate a pair of keys on your local machine, then copy the public key to the remote device's `~/.ssh/authorized_keys` file, you see.
This method is highly recommended for any production server or frequently accessed device. It dramatically reduces the risk of brute-force attacks, as attackers would need to guess your private key, which is practically impossible. Plus, you can add a passphrase to your private key for an extra layer of protection, making it very secure.
Using SSH keys also allows for automation. You can write scripts that connect to your remote devices without needing manual password entry, which is incredibly useful for repetitive tasks like backups or deployments. It truly streamlines your workflow, you know, making things much faster.
Using a Mesh Network Like Tailscale
For those who find port forwarding a bit too complicated or have dynamic IP addresses, a mesh network service like Tailscale can be a real lifesaver. Tailscale creates a secure, private network between your devices, no matter where they are located. It's like having all your devices on the same local network, even if they're physically miles apart, which is pretty cool.
From a remote machine that is part of the mesh network, use SSH to connect to the WSL distribution that is also part of the mesh network using its IP address provided by Tailscale. This completely bypasses the need for port forwarding and dynamic DNS services. You simply install the Tailscale client on each device, and they automatically connect to each other securely, which is really quite simple.
This approach is particularly good for accessing devices behind strict firewalls or for those who don't have direct control over their router settings. It provides a straightforward and secure way to SSH device from anywhere without the usual network configuration headaches. It's definitely worth looking into for a simpler setup, you know.
SSH on Your Android Device
Now that you’ve set up SSH on your Android device, it’s time to explore how to use it for managing IoT devices. This opens up a lot of flexibility, allowing you to carry your remote control capabilities in your pocket. You can connect to your home server, your Raspberry Pi, or any other SSH-enabled device directly from your phone or tablet, which is very convenient.
But how can you ensure a smooth and secure experience while using IoT SSH from anywhere on Android? The key is choosing a reliable SSH client app. Look for apps that support SSH keys, offer a good terminal interface, and have a strong reputation for security. Some apps even offer extra features like file transfer capabilities or connection profiles, which are quite helpful.
Using SSH on Android means you can perform quick checks, run commands, or even troubleshoot minor issues when you're away from your main computer. It's a powerful tool for staying connected to your devices and keeping them running, even when you're on the go. So, you know, it's pretty much like carrying a mini command center with you.
Frequently Asked Questions About Remote SSH
Is it safe to SSH into my device from anywhere?
Yes, it can be very safe, provided you follow best practices. Using strong passwords, SSH keys, and keeping your software updated are crucial steps. Also, consider changing the default SSH port and setting up a firewall. Improper setup, however, can create vulnerabilities, so, you know, always be careful.
What kind of internet connection do I need to SSH remotely?
To access your SSH device from anywhere, you need a stable internet connection on both your local machine and the remote device. The speed doesn't need to be extremely high for basic command-line access, but a reliable connection prevents frustrating disconnections. So, a consistent connection is really important.
Can I SSH into my Windows computer from anywhere?
Yes, you can. Newer versions of Windows 10 and 11 include an OpenSSH server feature that you can enable. Once enabled and configured, you can SSH into your Windows machine just like you would a Linux server. It's a bit different from traditional Linux SSH, but it works, you know, quite well.
Your Next Steps for Remote Access
Taking control of your SSH device from anywhere is a truly empowering skill. This comprehensive guide has walked you through every step, from understanding SSH and IoT basics to setting up remote access from anywhere, ensuring your IoT environment is secure, reliable, and accessible. You've got the knowledge to get started, so, you know, it's time to put it into practice.
Start by identifying the device you want to access remotely. Then, make sure it's prepared with the necessary SSH server software. Focus on getting your network settings right, especially port forwarding or considering a mesh network solution like Tailscale. Remember, security is paramount, so always prioritize strong authentication and firewall rules, which is really important.
You can learn more about secure remote access on our site, and link to this page for additional SSH tips and tricks. The ability to manage your devices from afar opens up a whole new level of flexibility and efficiency in your digital life. It's a skill that will serve you well, whether for personal projects or professional responsibilities, honestly.

Using Reclaim Cloud - GLAM Workbench
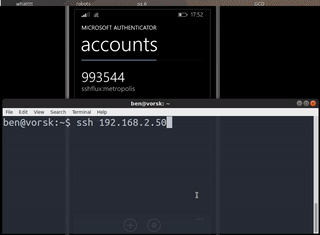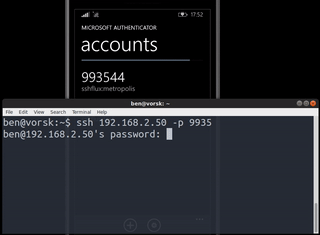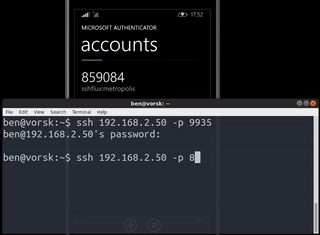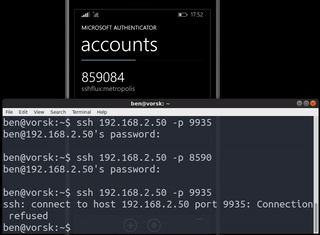
totp-ssh-fluxer o cómo tener un servidor SSH cuyo puerto a la escucha

5 Situs Penyedia SSH Gratis Server Indonesia | Sabadi Sayapku Blog